
Step-by-Step Guide: Collecting Basic Information Using Whois.com

Gathering Basic Information on Target Website Demo.cyberseclabs.org Using Shodan.com

How to Set Up a Monitoring System with Suricata: Complete Guide

Scanning the Network Using Nmap Tool – CyberSecLabs

CVE-2017-0144 (MS17-010) Exploit Tutorial for Educational Purposes

The Object detection with raspberry pi 5 complete guide for beginners Top Picks in 2025

Building a Cybersecurity Environment for Threat Detection and Defense — Detailed Installation Guide

Building a Home Lab for Cybersecurity Practice: A Step-by-Step Guide

How to Build a Raspberry Pi Honeypot System for Network Threat Detection

Why Your Cybersecurity Infrastructure Needs a Scalable UPS Solution: A Complete Guide

The Best ups for cyber security labs Top Picks in 2025

The Best fido2 hardware security token Top Picks in 2025

Complete 68 PicoCTF Challenge Solutions and Walkthroughs
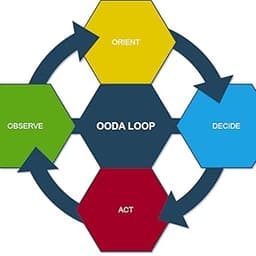
Top 10 Free Cyber Security Labs to Practice Hacking Skills in 2025

Face Recognition with Raspberry Pi and OpenCV: Complete Beginner’s Guide

How to Control TouchTunes with Flipper Zero: Full Guide & Setup

Flipper Zero Tutorial 2025: Best Beginner’s Guide (Easy Steps)

7 Practical Penetration Testing Labs from Basic to Intermediate Level

Scanning the Network Using Nmap Tool

Step by Step Exploit of CVE-2017-0144 (MS17-010)
Cyberseclabs.org is customer-supported. When you buy products through our site, we may earn an affiliate commission on featured products.
CybersecLabs.org
© 2025 Cyberseclabs.org. All rights reserved/
